Personal security concerns hit home when a virus cripples the family laptop or unseen forces steal Social Security numbers or bank account information, but director Alex Gibney’s Zero Days explores malware development with global ramifications. The film, showing July 22-24 and July 28 at Oklahoma City Museum of Art, provides valuable context for the concern that malware can be used to cripple essential infrastructure because, as Gibney deftly depicts, it already happened.
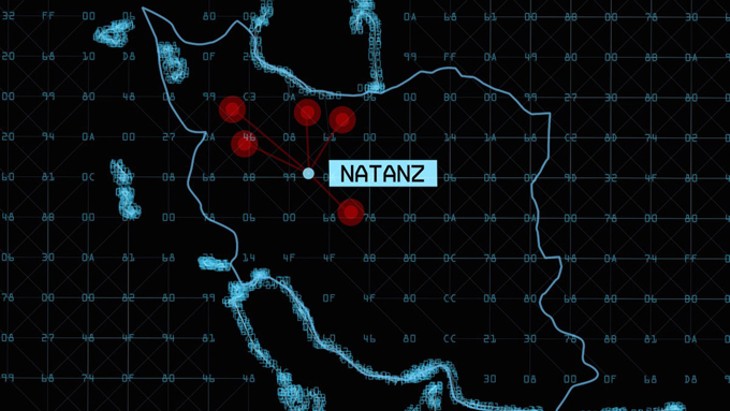
In 2010, a piece of highly sophisticated malware attacked Iranian nuclear facilities, and it was specifically programmed to wrestle control of Siemens programmable logic controllers (PLC), a highly specialized computer module designed for turning on and shutting off power plants, assembly lines or even amusement park rides.
The worm, which was dubbed “Stuxnet” in the press, contained insidious lines of code known to programmers and security experts as “zero days,” which allow the malware to act immediately without files being opened or other human actions.
The security company Symantec was the first to recognize Stuxnet’s patterns of infection, which spread worldwide but was highly concentrated at nuclear facilities in Iran. In addition to the “zero days” lines of code, Symantec analysts such as Eric Chien and Liam O’Murchu discovered that the malware was remarkably bug-free, indicating that this was not the work of some freelance cyberterrorist but the airtight programming created by a nation-state.
Gibney painstakingly illustrates how Stuxnet was proved to originate with Iran’s greatest enemies, the United States and Israel, and how the technology’s “zero days” coding allowed it to spread and ultimately land in the hands of volatile or disruptive powers like Iran and Russia.
The U.S.’s national security apparatus takes center stage shortly after Zero Days’ opening credits, with highly regarded former and current players waving off speaking directly about the program that the U.S. government called Olympic Games and the rest of the world knew as Stuxnet. As former CIA Director Michael Hayden said in the film, “By definition, it’s going to end up in this ‘we don’t talk about these things’ box.” As such, the U.S. government has never owned up to using an offensive cyberweapon, but in a 2012 classified executive order leaked by Edward Snowden, President Barack Obama said that any deployment of such a weapon requires the approval of the president.
As Hayden mentions during a press briefing excerpted in Zero Days, the 2010 Stuxnet cyber-offensive carries the distinct echo of August 1945, when the bombing of Hiroshima and Nagasaki, Japan, ushered in the nuclear era. A worm like Stuxnet can be used to take out a nation’s electrical grid, disrupt fuel pipelines, upset transportation systems such as trains or air traffic control and destabilize banking and internet traffic.
Gibney excels as a master of documentary horror, whether he reports on military use of torture, corporate malfeasance or highly organized and generously funded cults.
His latest film continues that string of informative excellence. Zero Days explains that, by taking away electricity, plumbing or even the internet that is responsible for far more consequential elements of modern life than just Twitter or email, a worm could bomb us back to the stone age without a single actual bomb going off.
Print headline: Tech wars, Alex Gibney’s Zero Days shows how a 2010 cyberattack began a new of era of weaponizing computer viruses on a global scale.